Fall 2024
Leadership Thoughts
The University of Pennsylvania’s Board of Trustees voted on July 31st, 2024 to approve the spinout of the Gene Therapy Program (GTP) effective October 1st, 2024. The Board’s approval kicked off a 62 day sprint conducted by a large, cross functional team to facilitate the transfer of staff, assets, technology, and data to two new startup companies, GEMMA Biotherapeutics and Franklin Biolabs. The formation of Franklin and Gemma is expected to accelerate the future of gene therapy and help expedite the delivery of new therapies to patients.
While planning discussions took place for several months among key areas of the organization, successfully launching the two companies required strong collaboration across the University, Health System and PSOM, from senior leadership, Penn’s Office of General Counsel (OGC), the Penn Center for Innovation (PCI), Penn Information Systems & Computing (ISC), PMACS, Penn Medicine IS, Human Resources, and Space Planning and Operations. Working alongside RSM, an external transition assistance company, the team achieved multiple objectives., Space was leased within Discovery Labs and TRL. Assets were relocated to support both companies’ new operations. Also, research equipment and data were transferred. From an IT standpoint, over 40 PMACS and Penn Medicine IS staff contributed to the activity in a variety of ways. PMACS, Penn Medicine IS, and ISC worked closely to remove all University owned network and telephony equipment from Discovery Labs and convert the Gemma staff at TRL to a new network operated independently of Penn Medicine. The teams successfully transferred over 300 terabytes of data from multiple Penn Medicine systems including the high-performance computing cluster (HPC), SharePoint, email files, file shares, and home drives.
In addition, Penn worked with Franklin to facilitate the use of several Penn-hosted research applications until Franklin could convert to their own systems. The team then had to pursue license modifications and configuration updates to provide extended access to the new companies during the transition period. Because there were limitations on which data was transferred to Franklin and Gemma, IS, OGC, PCI, and GTP staff had to work together to implement rules to separate data before it was migrated.
The many IT teams supporting the project worked tirelessly, logging additional hours on nights and weekends to ensure completion of the transition by the October 1st date. The project is an excellent example of our teams collaborating and working together to deliver on a key initiative in an extremely tight timeline. We extend our sincere gratitude and thanks to all those that contributed to the GTP separation project.
Chris Dymek, Entity Information Officer
Meredith Fetters, Associate Chief Information Officer, Research Information Systems
Employee Announcements
Wallace (Wally) Wormley
Wallace (Wally) Wormley has been promoted to Director of the Abramson Cancer Center’s One Cancer Research Data Technology team. With 18 years at the ACC and 22 years at the University of Pennsylvania, he has significantly contributed to developing cancer research-related software and databases. His leadership has been pivotal in advancing multiple areas and specialties within the institution. In his new role, Wally will remain in PMACS Software Development, but will have an additional reporting relationship to Dr. Katherine Nathanson, ACC Deputy Director, and work closely with Dr. Peter Gabriel, Associate Director of Clinical Informatics. Congratulations to Wally on the new position!
LIMS Team Supports Infectious Disease Effort to Share Live Data Dashboards
The LIMS team has partnered with Dr. Brendan Kelly’s Infectious Disease Laboratory to share up to date data metrics about their biobank with collaborators. The LabVantage system was configured to send weekly data reports that populate research specimen inventory dashboards on the Infectious Disease website. This is a first of many anticipated types of web-based sharing of data from the LIMS. Below are a few examples of the dashboards found at https://motionlab.site/cstar.html.
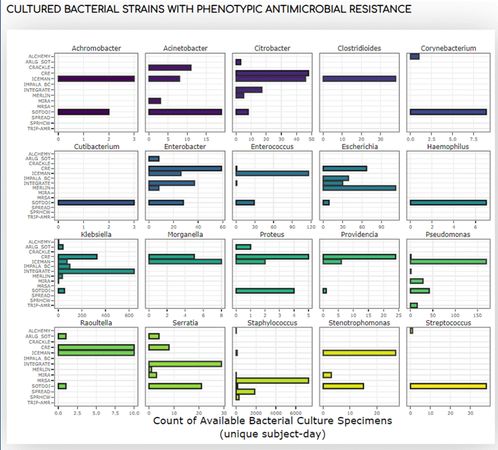
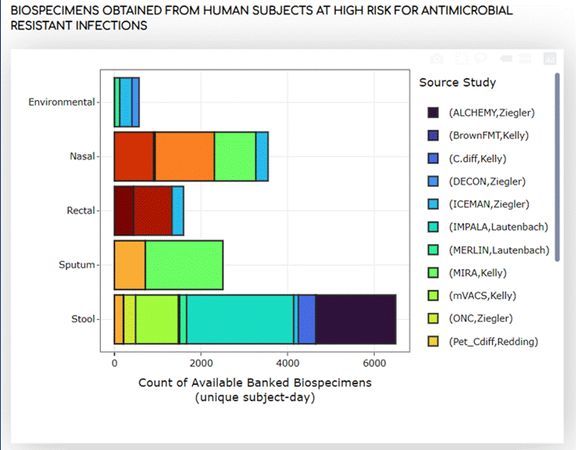
MathWorks Transitions to Single Sign On (SSO) Logons for Matlab Licenses
MathWorks, the publisher of Matlab, is transitioning all of its higher education customers to use of Single Sign On (SSO) for access to resources on their web site. The University of Pennsylvania transitioned to SSO on November 6, 2024.
What does this mean for you?
First, if you are using a Matlab license that has been installed and activated on a desktop or laptop computer your use of that license will not be impacted by the transition to SSO.
Once SSO is turned on login to MathWorks will be through PennKey WebLogin.
Follow these steps the first time you login to MathWorks after SSO is enabled to access an existing account or to establish a new one:
- Visit www.mathworks.com and click “Sign In”.
- You will be prompted to enter an email address: Enter your upenn.edu email address.
- You will be taken to the PennKey Single Sign On page to enter your PennKey and Password.
- You will be prompted again for an email address: If you already have a MathWorks account, enter the email address associated with that account. If you do not yet have an account enter the upenn.edu email address you would like associated with your account.
Please reach out to the Office of Software Licensing (licenses@upenn.edu) with any questions or if you encounter any issues accessing your MathWorks account.
Verified Duo Push Now Required for PennKey Single Sign On (SSO) Applications
To improve the security of PennKey SSO applications including Microsoft O365, on October 23, 2024, Verified Duo Push replaced Duo Push. This change only applies to users who currently use Duo Push as their second factor for authentication. See below for details.
Enhanced Security
Duo Push is one of the ways users can complete the second step of Two-Step Verification when logging into a PennKey-protected service. For users with Duo Push enabled, a notification is sent to the user’s smartphone or tablet to verify identity. Instead of clickable “Deny” or “Approve” options, with Verified Duo Push the user is required to enter a three-digit code (see images below). The code gives added protection against “push harassment” and “push fatigue” cybersecurity attacks where users are spammed with push requests until they reply “yes.”
What Changed
Only the Duo Push process to establish a PennKey SSO session or log into Microsoft O365 will change. Users will continue to use the Duo Mobile app and other login options as they do today. Changes include:
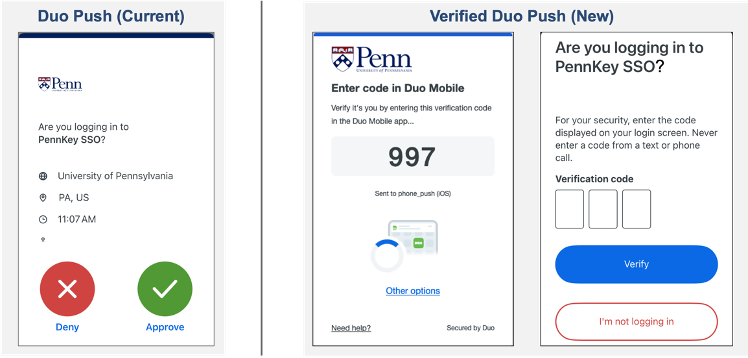
-
Users who use Duo Push will be shown a code to enter on their mobile device when responding to the Push instead of the “Deny/Approve” buttons.
-
Users who do not have Duo Push enabled will still be able to log in the way they do today to access PennKey SSO applications. These users are strongly encouraged to adopt Push to take advantage of the better protection.
Help & Resources
- Access ISC’s Two-Step Verification help documentation.
- Users can find support contacts on the Two-Step Verification help contacts page.
- Support providers may contact ISC Client Care for issues.
Cybersecurity Update on Email Spoofing
More likely than not, you’ve been a target of email spoofing at least once in your life. That’s because email spoofing targets everyone, from an individual to multi-billion-dollar companies.
Email spoofing is a technique used by cybercriminals to make an email appear as if it was sent from a trusted source, when in fact it was sent from a different, often malicious, source. This is commonly used in phishing attacks to trick recipients into providing sensitive information, such as passwords or financial details, or to spread malware.
Stay vigilant and always verify the authenticity of emails, especially those requesting sensitive information or urgent actions.
Here are a few key points about how to identify spoofing email.